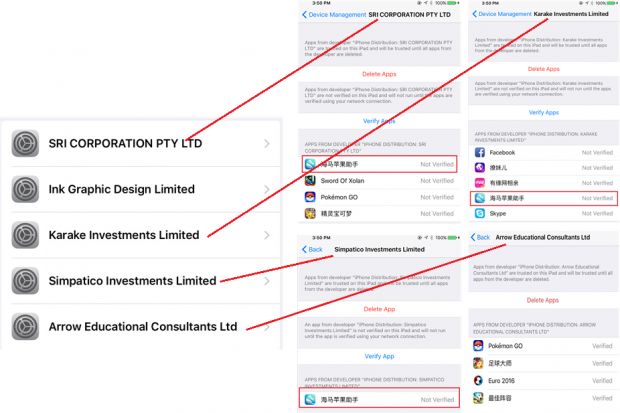
Apple supports App side-loading for the enterprise market to ensure that employees of private companies get the opportunity to use necessary files for customized applications that are not available in the App Store. Typically, such programs contain corporate information, and Apple will only benefit from the side-loading, as in this case, its devices can be used by the employees of enterprises in the workplace. Chinese service Haima uses side-loading to spread adware. The installation process of the applications is very complex and is based on the Apple issued corporate certificates. Typically, fraudsters make users go through the entire procedure, using social engineering techniques. In the case of Haima service is switched from one enterprise to another certificate in every three days, since Apple regularly blocks the fake certificates. As a rule, cybercriminals buy stolen certificates on underground hacking forums. The average value of the goods is about $300, yes now just think that how much Haima adware earns. As the security experts of Trend Micro explained that all distributed through the application Haima contain dynamic code responsible for displaying advertisements, usually by InMobi, Mobvista, Adsailer, Chance, DianRu and Baidu. In some cases (for example, in “clone” of the game Pokemon GO), this code also introduces fake GPS data, providing users with the ability to play even in unsupported areas. From this, it follows that the process is not automated, and the developers need to manually implement the code in your application. According to Trend Micro, over 75 million iOS users have installed apps from the Haima store. Yes, it means that more than 68,870,000 users have already downloaded a modified version of Minecraft Pocket Edition, another 6+ million installed a tampered version of the Terraria app, while over one million installed the previously mentioned Pokemon GO app.